Welcome back to the Lync 2010 Edge Server discussion.
In Part 1 – We added the Edge to the topology and did all the prep/install work.
In Part 2 – We did the Internal Certificate Work.
This time, we'll do the External Certificate Work and final environment prep.
Okay, if you remember, we left off here…
We have setup our edge, configured everything, and are now working on certificates. Last time we did the "internal" certificate. This is the one that the Edge uses to communicate to the Front End/Pool to replicate topology/CMS information. Now it's time for the "external" certificate – for the public facing portion of the Edge.
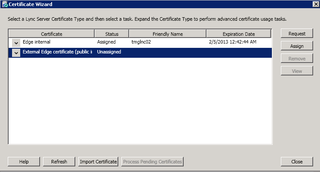
Highlight External Edge and click Request
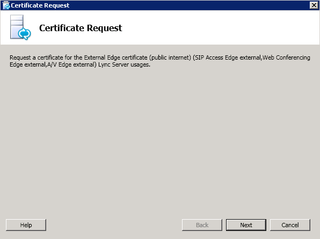
Yup, Next.
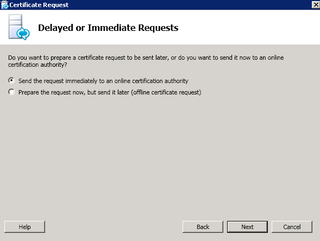
We are going to prepare the CSR later. Choose that and click Next.
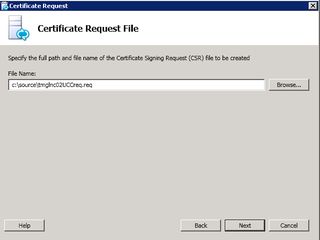
Save the file somewhere useful – like, say, C:source. Click Next.
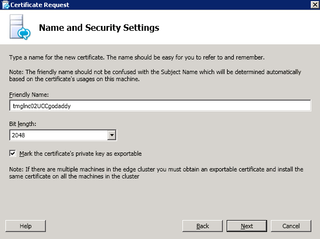
Friendly name (so you can identify it later), 2048, Exportable Key. Click Next.
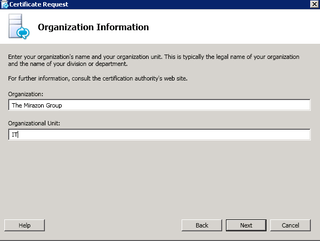
Info. Next.
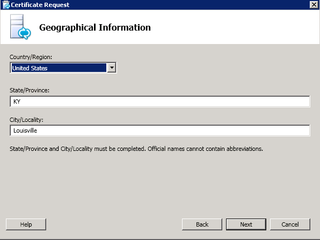
Info. Next.
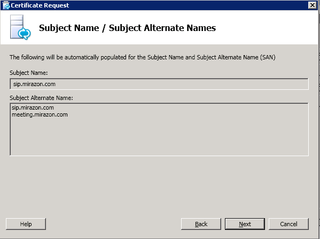
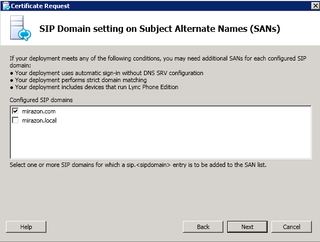
It automatically populates the "sip" and "external web services" name. Next.
We're just using mirazon.com as our SIP URI info. Next.
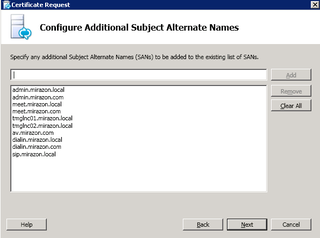
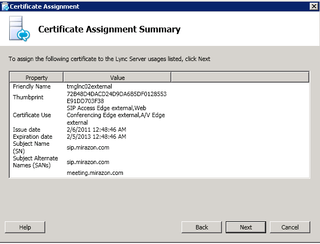
Add any other relevant SANs. You'll nee the SANs for any URL you've entered in your topology – like Edge AV, Edge Conferencing, etc. If you are going to share this public cert with the External Web Services access (TMG) like we are, add those here. For Mirazon, we've chosen to use this single cert everywhere. This goes back to the Lync Mac Users question I received. I didn't have to add anything to the MacOS keychain because I'm using a public cert for the various webservices. Anyway, enter the relevant SANs based on your topology/URLs and click Next.
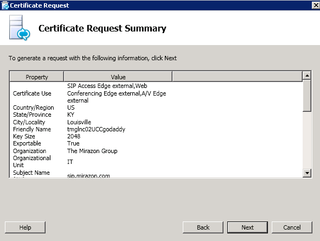
Verify, click Next.
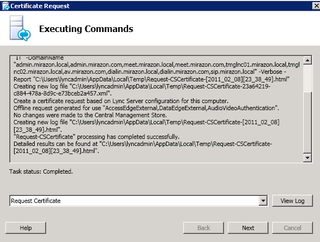
Great. Now you've created your certificate request. Go get it and bring your provisioned certificate back.
//NOTE// I've lost a few screen shots, so these aren't going to match. Sorry.
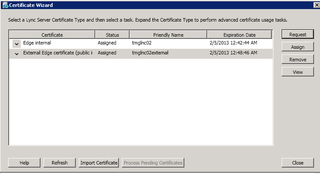
After you've imported your certificate (screen shots lost) you can assign it. Highlight external Edge certificate and click Assign.
Click Next.
Choose the right certificate (missing screenshot, this one above was from an earlier process), click Next.
Great. Done. Finish.
Great, you've now assigned your certificates to the External edge too. Click Close.
Great! Now, Start Services.
Next.
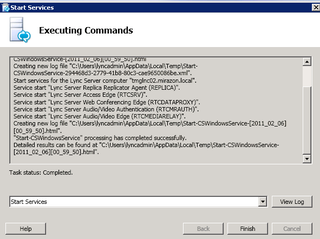
Excellent. The 5x Lync Edge servics are now going to start. Click Finish.
I now need to create some PUBLIC DNS records.
For "Edge Access" to work, you need to create the following A Records (missing screen shots)
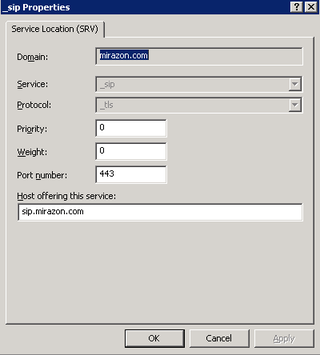
sip.mirazon.com -> pointing to my External Access Edge NAT'd IP
conf.mirazon.com -> pointing to my External Access Conferencing NAT'd IP
av.mirazon.com -> pointing to my External Access AV NAT'd IP
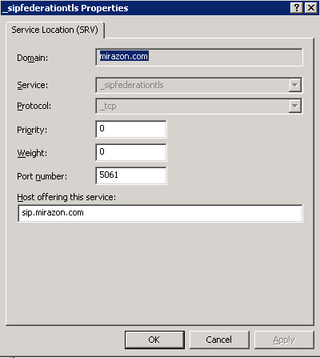
You also need the autodiscover records for both SIP/Client access and Federation (optional)
The following record is the Autodiscover SRV Record for Lync Client access from the outside.
Finally, the Federation SRV Record
Great. We now have a fully functional Lync 2010 Edge Server – in a perfect world 🙂
I liked the guide. Have been following this for testing, but.. You use meeting, meet, conf, etc. Is this intentional, or is it suppose to be consistent throughout?
Following this guide, we set up “meeting”.mirazon in the federation-server, “meet”.mirazon in the edge and certificate, and finally, you NAT “conf”.mirazon?
/Confused…
Greetings Daryl,
I am interested in knowing how this setup has turned out since so many other articles indicate Lync Edge Servers REQUIRE 2 NIC’s & IP’s on separate subnets.
I would very much like to know how to handle the NAT translation for a single public IP to the 3 private IP’s for SIP/web/AV and their associated ports.
Any help you could provide would be very much appreciated.
Regards,
Andy