One of my latest projects has been to change all the login / enable passwords for our various Cisco routers and switches. We've had some turnover, and frankly, they haven't been changed in many many years.
So, I had one of three options:
- simply change the login passwords and enable passwords. easy.
- move to local database user(s) instead. easy too.
- move to AAA / RADIUS authentication based on Windows 2008 NPS. a little tricky.
I chose the third option.
Why? I like a challenge. No, not really. I chose that because it will make it easier to adjust/change access to the devices whenever we have staffing changes, or whatever. Using Windows 2008 NPS will utilize an Active Directory group – just like all of the other RADIUS stuff we do. It's something we're familiar with.
Let's get going…
First of all – giant shout to @hezetation for this. Hez & I are friends and we worked together at a previous employer AND he's a very sharp Cisco / Apple guy (what? you can like both Cisco & Apple at the same time?). As I got going, and then eventually stuck (more on that later) – Hez was a great resource. Two thumbs up. Thanks dude!
Cisco Config
So – let's get going on the config changes needed for the Cisco gear. The below is the example from my home router – a Cisco 871W that gives me internet access and also VPN acces back to the "home office" in Oklahoma.
First of all, we need a local username – so we can still get to the devices incase RADIUS goes down
#username <username> privilege 15 password 7 013B072C5A26070B2475411C350A18192218313A6A671F1A1B
Next we need to add the actual AAA (Radius) stuff.
aaa new-model
aaa authentication login <group name> group radius local
aaa authorization exec <group name> group radius local
Next we'll adjust the radius access itself
ip radius source-interface bvi1
radius-server host <ip address> key 7 013B072C5A26070B2475411C350A18192218313A6A671F1A1B
Finally we'll change the config for the con / vty ports
line con 0
authorization exec <group name>
login authentication <group name>
line vty 0 4
authorization exec <group name>
login authentication <group name>
That's it. Seriously. You're done on the Cisco side.
Windows Server 2008 NPS Config
This was the trickier part. In our environment, we're already using Windows Server 2008 NPS for our Cisco VPN & Ruckus Wireless setup. All I'm doing here is adding additional functionality. No problem. Let's get going.
Let's start by creating some clients – these will be our various Cisco Devices – routers & switches and such. Head over to NPS – Network Policy Server applet, expand on RADIUS Clients and Servers, Right-click on RADIUS Clients and choose New.
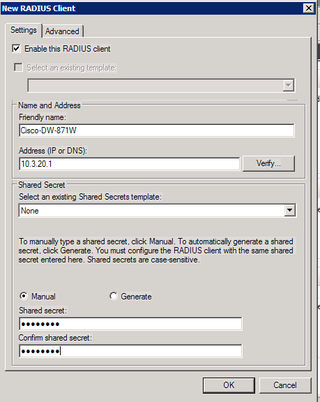
Yup, just like that. Now, let's enter useful information.
Notice that I'm starting my "Friendly name" with "Cisco-" (more on that later). The shared secret is the same shared secret that I entered above in the Cisco config section under radius-server key. They need to match. Click on the Advanced tab.
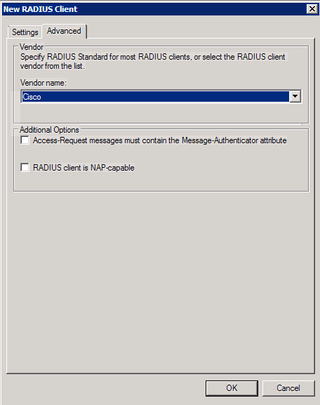
Let's choose the Vendor Name of Cisco. This DOES work with "RADIUS Standard" – but – for fun – let's choose Cisco. We're done. Click OK.
Now, head back to the NPS. Right-click on Network Policies, and choose New.
Alrighty, here some screen shot galore. Follow along.
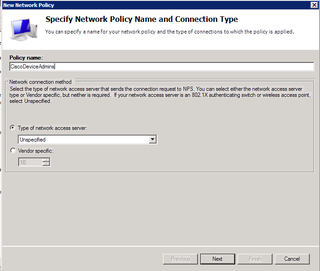
Give your new policy a name – something useful to you so you know which one it is – especially if you have several different policies. Unspecified is fine for the type of NAS. Click Next.
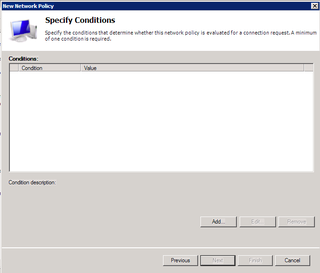
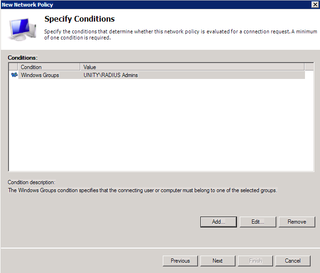
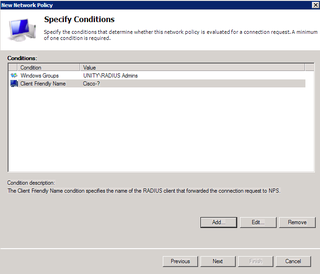
Okay, let's add some conditions. Click Add.
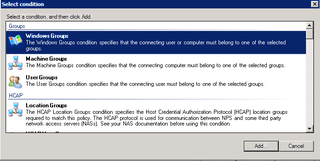
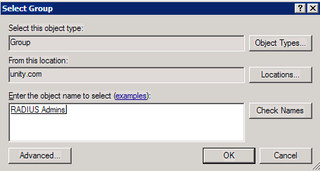
We'll restrict login to people based on AD membership – so – choose Windows Groups, and click Add.
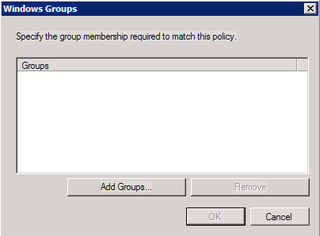
Click Add Groups
We want RADIUS Admins – Click OK. Click OK again.
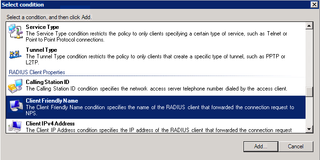
Good. Now, we also want to apply this to the various RADIUS Clients that are important to us – you know, the ones that start with "Cisco-" – click Add.
What we want is "Client Friendly Name" – Click Add.
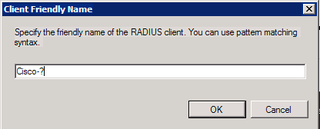
And we want any RADIUS client that starts with "Cisco-" – so – enter "Cisco-?" and click OK.
Looks good so far. Click Next.
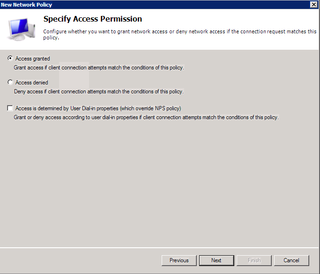
Access Granted. Yes please. Click Next.
Make sure PAP is checked. Click Next. No need to read the "help" if you don't want.
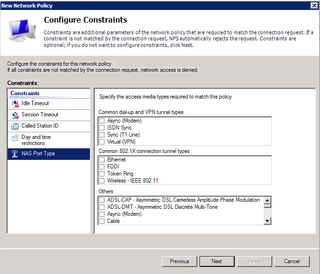
No constraints to deal with. Click Next.
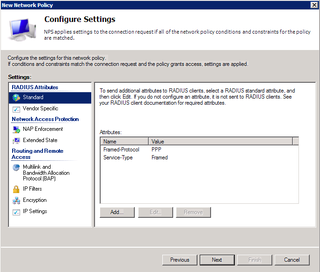
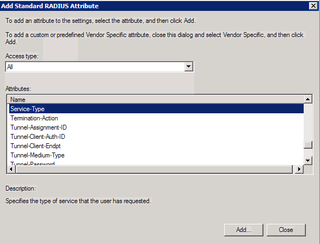
Here comes the fun. Remove both the PPP & Framed attributes. Then click Add.
Choose Service-Type. Click Add.
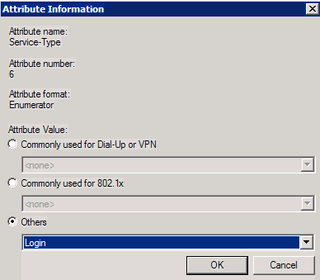
Choose "Others" and "Login" – Click OK & Close.
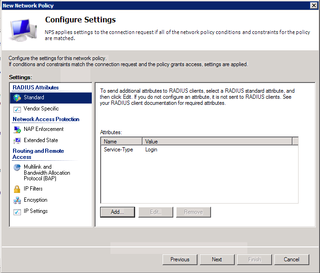
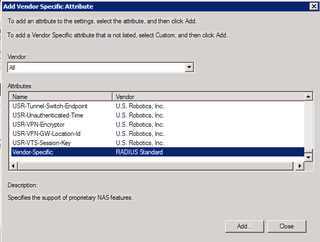
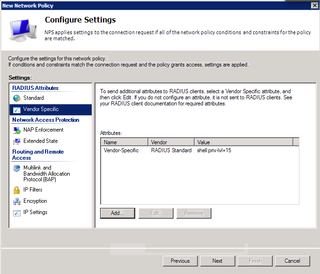
That's all for Standard. Now, click on Vendor Specific.
Great. Click Add.
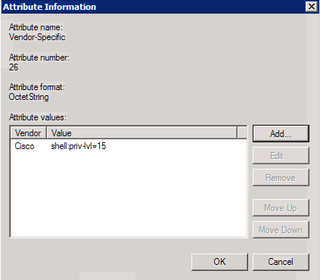
Choose Vendor-Specific and click Add.
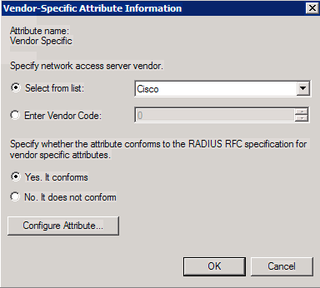
Choose "Cisco" as your vendor. Yes, this conforms to RADIUS RFC. Click Configure Attribute.
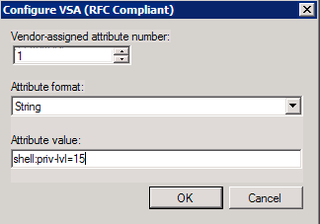
This string is what gives successful authentication "enable" or "privilege 15" access on the Cisco gear. Make the appropriate changes. Click OK. Click OK again.
Looks good. Click OK again. Click Close.
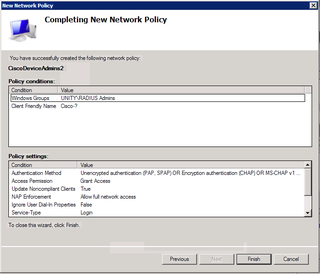
I used the defaults for all the rest of the NAP / RRA stuff above. Click Next.
All that looks good. Notice my name here is "CiscoDevicesAdmins2" – this is the 2nd time I did this and I cannot find my first screen shot. Pay no attention to that. Oopsie! :) Click Finish
Let's Test
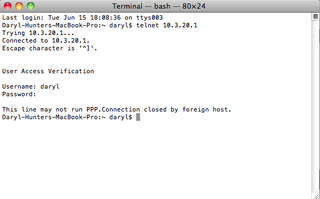
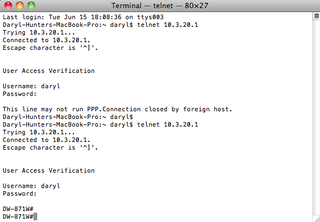
Great! Now, let's test this sucker. We're going to telnet to my 871W router – 10.3.20.1 is the IP address. Let's go do it! Drop to terminal…
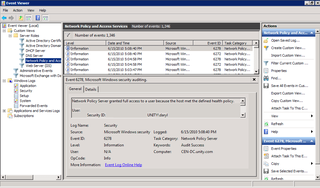
What? "This line may not run PPP." What does that mean? Let's go check out the logs on NPS first.
Here's the log entry. As I look at it more closely, I'm granted full access. NPS did it's job. What in the world? Why can I not get access to my router? Time for some Google-fu…
<PAUSE FOR 2 DAYS OF HEAD BANGING>
So, as you google for the phrase "This line may not run PPP." as it relates to Cisco / RADIUS, you'll find a ton of people with the same problem. And, all of them have this issue on Server 2008 NPS. Why is that?
Well, this is where @hezetation becomes a hero! He lets me screen share his setup and poke through each and every window and session and attribute. Our Network Policies are identical (minus the name). So, we then talk about "global" policies and Hez has an "ah ha!" moment…
The Fix
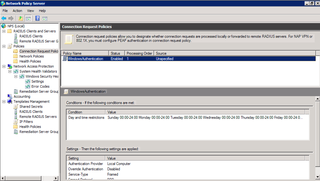
So, I have a single Connection Request "global" policy – let's go to NPS and look at that.
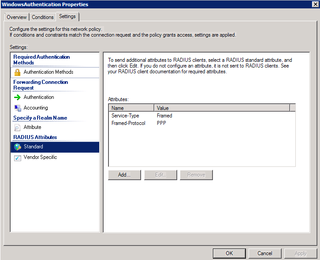
The "WindowsAuthentication" policy overrides the others with certain settings… so… go to properties, Settings…
Check that out. PPP. Right there under RADIUS Attributes -> Standard. I don't need that. I have specific Network Policies to handle VPN/RADIUS and such. Let's remove both of those – the PPP / Framed settings and click OK to apply the changes.
Test Again
Right – now – let's test again… drop to terminal…
SUCCESS! YAY!
Okay – so – that's that. I had the policy and Cisco configs right. What I missed was the fact that under Server 2008 NPS, the Connection Request Policy settings could override (globally) individual Network Policies. Good info to know.
Next step – figuring this out for our various Dell PowerConnect switches (random 3000 and 5000 and 6000 series) that we have in production… won't THAT be fun…
//Update 9-15-2010 – I have added our various Cisco 1100 series APs into our AAA / RADIUS (admin) setup and these instructions worked the same way as they did for routers / switches / etc. This works just fine.
Hope this helps someone.
You can also do Cisco-* in client friendly name field, either one works but might be some long time windows guys to remember the ol * for anything following.
Hey, did an Apple guy just write that?! 🙂
Bless you! This was the exact solution I was looking for. Thanks for making a clear and concise guide w/ troubleshooting! You da man!
No worries Aaaron! Glad it was helpful. I refer back to this post often when doing this for other customers.
YOU ARE MY HERO! LOL
Thanks, Brother! I really appreciate your sharing this. This was just the walk through I needed. We are currently running RADIUS on our W2K3 servers but are (finally) getting around to migrating to W2K8 R2. Awesome testimony by the way. For those that haven’t seen it, I recommend reading Darryl’s blog on Faith.
Also, I was listening to the radio yesterday. If you haven’t heard of the blog “Not A Fan” it speaks a great deal about many of those things you mentioned in your testimony. God is truly moving in His people now. Let’s pray that we will see this as the beginning of the next GREAT AWAKENING!!! 2 Chronicles 7:14
Hi, such a luck to find you!
Actually I face another very interesting issue with our CISCO ASA 5500 + Win2008R2 + NPS, I wonder if you can help me?
It is that we implemented an authentication server that sends out OTP SMSs to the user they can then use to get in to the VPN.
The problem is that CISCO ASA 5500 has a config paraneter for AAA servers called retry-interval that can only be set up between 1-10 sec.
So our current config looks like this:
hostname(config)# aaa-server srv1 protocol radius
hostname(config-aaa-server-group)# aaa-server srv1 host 1.2.3.4
hostname(config-aaa-server-host)# timeout 20
hostname(config-aaa-server-host)# retry-interval 10
Because sending out the SMS OTP usually takes more than 15 sec it results in CISCO automatically sending out a repeated radius request so the AAA server generates another OTP and sends out another SMS still for the same login request.
Is there any way to set up the system (any part, either CISCO or NPS) to only forward a login request for the same user not earlier than eg. 60 sec?
Your advice would be highly appreciated.
Best regards,
Gyozo
awesome dude. thumbs up for you
Thanks for the post, just what i was looking for.
Thanks for putting this up. A couple of comments:
(1) While you’re troubleshooting, if you have more than one RADIUS network access policy, try changing the order they’re applied in. I bashed my brains out troubleshooting a policy for two days, then fixed everything by moving it up in the order of policies. Turned out the culprit was the policy right above it–which was actually doing what I wanted, just too much of it.
(2) I’m not so sure about setting the RADIUS attribute “shell:priv-lvl=15”. It’s convenient but risky: on every device, anyone with the right credentials gets godlike powers the minute they walk in. I think better to configure it on the devices themselves as appropriate. Sometimes you want godlike powers from the get-go, sometimes you want the option of harmlessly looking around first–stethoscope first, THEN the chainsaw.
Thank you. This blog helped me a lot.
Hi, just a question on the Cisco side. What would the ‘Group Name’ match up with on the windows server side? ‘Cisco Admins?
Thanks!
HI Dary,
I wounder if you have done it and can provide me some help. Although I still have not given up, but I tried configuring NPS for 802.1x port-based authentication with Cisco Catalyst 2950 switches and so far I did not have any luck. The logs in NPS show that authentication failed, but my configurations for client and server certificates are all right. I did some google search and there are people with the same problem for some of them it works today, but fails tomorrow. I suspect there mus some configuration required on NPS to get this work.
Thanks for your post, I will definitely try it.
Sir, you are AWESOME!!! This tutorial helped me a lot.Thanks!!!
I could setup it and authenticate, however teh user logs to Cisco without privilege. If I try enable command it does not accept the password.
Thanks for sharing, great article.